Discover Cutting-Edge LinkDaddy Cloud Services: A Press Release on Advancements in Cloud Technology
Discover Cutting-Edge LinkDaddy Cloud Services: A Press Release on Advancements in Cloud Technology
Blog Article
Protect Your Info With Top-Notch Cloud Storage Space Provider
Utilizing excellent cloud storage space services can give a robust shield versus possible dangers and susceptabilities that might compromise your data. By checking out the sophisticated safety and security features and file encryption protocols provided by respectable cloud storage suppliers, you can strengthen your defenses and make certain the confidentiality and honesty of your sensitive details.
Relevance of Secure Cloud Storage Space
Protected cloud storage is critical in safeguarding delicate data from unapproved accessibility. By using encryption approaches and robust gain access to controls, cloud storage space carriers guarantee that just authorized users can access sensitive info, reducing the risk of information violations and cyberattacks.
In today's interconnected world, the demand for protected cloud storage space has never been much more critical. Whether it's personal records, economic documents, or proprietary company info, ensuring that information is kept safely in the cloud is important for maintaining privacy and conformity with data security laws. In addition, secure cloud storage permits for smooth partnership amongst users while maintaining strict safety protocols to avoid unauthorized gain access to.
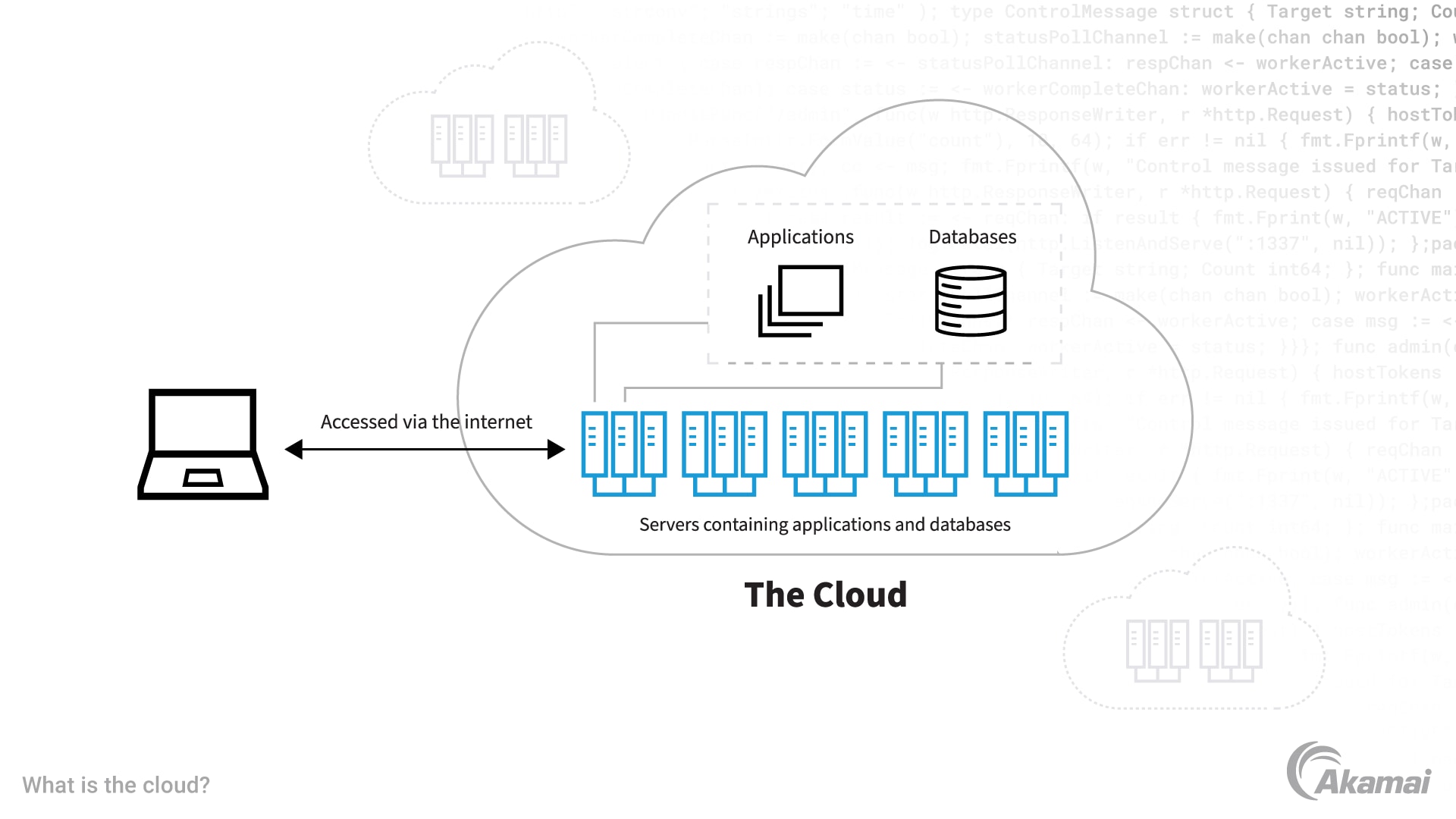
Features to Seek
When evaluating cloud storage solutions, it is essential to take into consideration essential functions that boost information safety and use. One crucial feature to seek is end-to-end file encryption, which makes certain that data remains encrypted from the minute it leaves your gadget up until it reaches the cloud server - linkdaddy cloud services press release. This encryption technique considerably decreases the risk of unapproved accessibility to your delicate details
Another necessary attribute is two-factor authentication, which includes an added layer of protection by needing not only a password and username yet likewise a piece of information that only the customer has access to. This substantially reduces the opportunities of unapproved gain access to, even if login qualifications are compromised.
Additionally, durable accessibility controls are vital for guaranteeing that only licensed people can view, edit, or erase details data within the cloud storage. Granular permission setups permit modification of accessibility levels, boosting information security and privacy.
Finally, normal data backups and versioning abilities are essential attributes to consider, as they make certain that your data can be conveniently recovered in situation of unexpected deletion, corruption, or a cyberattack.

Advantages of Information Security
Data file encryption plays a crucial duty in protecting sensitive details stored in cloud solutions, enhancing overall information protection. universal cloud Service. By converting data right into a code that can just be accessed with the right file encryption key, security makes sure that also if unauthorized individuals acquire access to the data, they can not understand it. This process includes an added layer of protection to secret information, such as personal information, economic records, and organization tricks, making it substantially harder for cybercriminals to abuse or steal the information
One of the key benefits of data security is that it assists companies comply with data security laws and market criteria. By encrypting information saved in the cloud, business show their commitment to information safety and reduce the danger of possible penalties or lawful consequences for non-compliance.
Multi-Device Access

Multi-device availability enhances productivity and collaboration by allowing users to work with the same data from different tools without the need for hands-on transfers or compatibility issues. This feature additionally makes sure that crucial information is readily offered and always current, irrespective of the tool being made use of. The seamless combination of cloud storage solutions with different operating systems and devices contributes to a smooth user experience, advertising performance and adaptability in taking care of digital properties.
Data Healing and Back-up Solutions
Implementing robust information healing and backup options is essential in making certain the safety and security and integrity of important digital possessions - Cloud Services. In today's digital age, where data loss can arise from numerous elements such as equipment failure, human error, malware strikes, or all-natural catastrophes, having a dependable backup and recovery strategy is essential for individuals and companies alike
One of the essential facets of an effective data recovery and back-up remedy is normal backups. By scheduling automated back-ups of data to a safe cloud storage space solution, organizations can decrease the risk of information loss and ensure that details navigate to this site is quickly retrievable in the occasion of an unexpected incident. In addition, executing an extensive information healing strategy that includes routine testing and recognition of backups can aid identify and address any type of potential concerns before they rise right into crucial information loss situations.
Moreover, security plays an essential duty in safeguarding backed-up data, ensuring that delicate details continues to be secured from unauthorized gain access to. Selecting a cloud storage service that uses durable encryption procedures can provide an additional layer of security for stored information, giving users comfort recognizing that their info is safe and easily accessible when needed. By purchasing dependable data recuperation and back-up individuals, companies and solutions can secure their electronic properties and mitigate the impact of unpredicted information loss incidents.
Final Thought
Finally, making use of top-notch cloud storage space solutions with features like data security, multi-device accessibility, and information healing solutions is vital for safeguarding sensitive details from unapproved accessibility and ensuring information integrity. By focusing on information safety organizations, actions and individuals can improve their general cybersecurity pose and abide with data protection laws. Applying protected cloud storage space solutions is crucial for advertising and safeguarding electronic assets efficiency and cooperation in today's digital landscape.
Whether it's personal records, monetary records, or proprietary organization information, making certain that information is kept securely in the cloud is necessary check out here for keeping personal privacy and compliance with data defense guidelines.Data security plays a critical function in protecting delicate info stored in cloud solutions, enhancing overall data safety and security. By securing data saved in the cloud, firms show their commitment to data safety and security and reduce the threat of prospective penalties or legal effects for non-compliance. By scheduling automated back-ups of data to a safe cloud storage pop over to this site service, organizations can reduce the threat of information loss and ensure that info is conveniently retrievable in the occasion of an unforeseen case.In conclusion, making use of top-notch cloud storage solutions with features like information encryption, multi-device ease of access, and information recovery remedies is critical for safeguarding sensitive details from unapproved access and making sure information stability.
Report this page